Analysis file artifacts
The Events report section displays additional artifacts that the VMware backend gathers while it process the sample. These artifacts are included in the report for you to download:
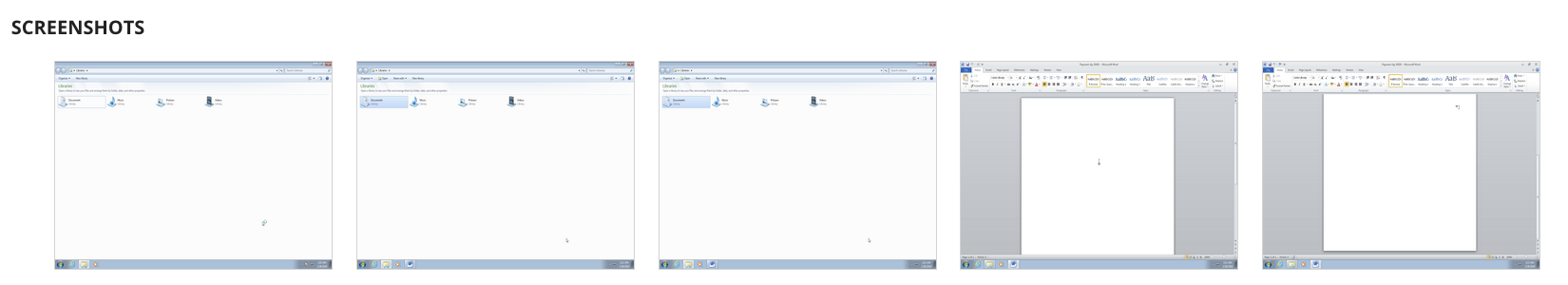
- Screenshots
-
Multiple screenshots are taken while the file is being analyzed. These screenshots give you an overview of the graphical activity of the subject.
For sandbox analysis, the VMware backend takes screenshots of activities on the desktop. Screenshots could be found in the analysis type Windows 10.
For URL analysis, the backend takes screenshots of the rendered Web Page in a browser. Screenshots could be found in the analysis types Chrome or the simulated browser.
For PDF analysis, the backend takes a screenshot of the first page of the PDF document. Screenshots could be found in the analysis type Simulated file viewer.
- Packet capture
-
If the subject generated network traffic, this traffic is collected and saved in a
pcapfile. - Extracted files
-
For an inflated archive, a list of the contents is displayed. Each row shows the Mime type, Tag (indicates the type of analysis), Description, Filename (if available from the archive), and Score of the artifact. A score is provided only if the artifact was analyzed. In this case. a link to its report is also provided.
See Handling of Containers in the API guide for more information.
If the VMware backend encountered an error when unpacking an archive, it displays an alert indicating the error condition. Errors include maximum file limit exceeded, maximum depth limit exceeded, and maximum child task limit exceeded.
- Generated files
-
During analysis, the sample may generate various files. These are displayed in a list sorted by Path:
- Path: The path of the artifact in the file system.
-
Type: The determined file type. Click to sort the list by file type.
Click the icon to expand a row. Data for MD5, SHA1, Size (bytes), Packers, and Signatures are displayed. Data may not be available for all fields.
Click the icon to download the script to your local system.
- Decoded command line arguments
-
The arguments to malicious PowerShell scripts are often encoded or obfuscated. If a script was executed during the analysis, the VMware backend decodes it, making its arguments available in a more human-readable form. These arguments are displayed in a list showing the Analysis subject and Decoded script.